 at GISEC 2024
at GISEC 2024 Security Control Validation.
Supercharged.
FourCore ATTACK proactively tests your cyber defenses by emulating real-world threats and improve them with actionable insights in real-time.
Trusted By



Real Threats. Real Response.
Why FourCore for Adversary Emulation?
FourCore ATTACK is a Comprehensive
Adversary Emulation Platform
Adversary Emulation
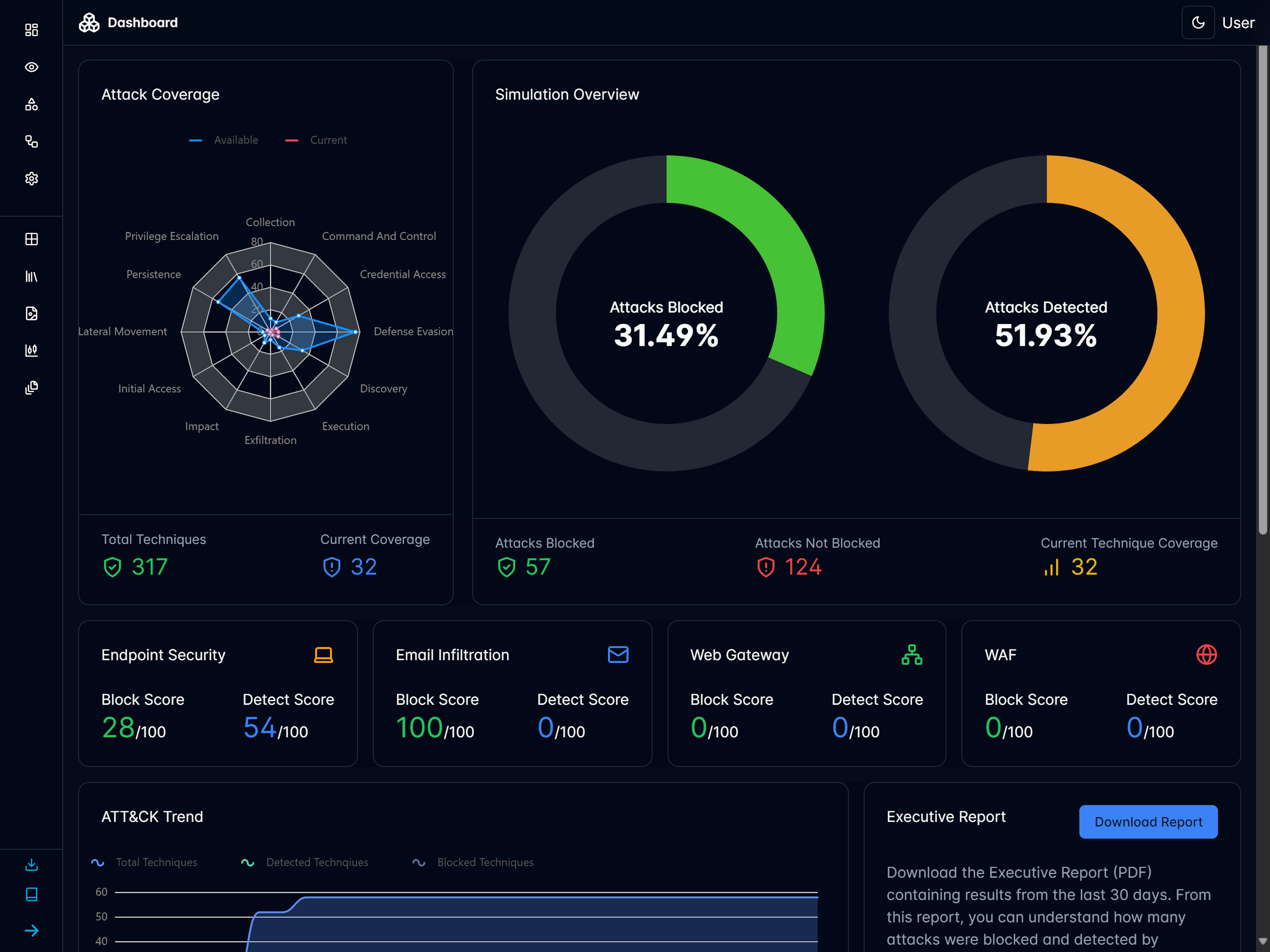
Realistic threat emulations give you the information and IoCs to identify the true risk in your environment.
MITRE ATT&CK® Coverage
Test and validate thousands of procedures for more than 300+ MITRE ATT&CK® Techniques.
Multi-Domain Testing
Comprehensive validation of the defense surface across endpoint, network, email and web security solutions.
Automatic Correlation
Correlate alerts in your security solutions to emulated threats automatically with API Integrations.
In-Depth Evidence
Gather real evidence (IoCs, Outputs, Logs) to verify if cyber defenses were able to observe, detect and prevent threats.
Actionable Insights
Improve your defenses with knowledgebases, detection rules and actionable recommendations.

Yes, FourCore integrates
with
FourCore ATTACK enables bi-directional sharing and enrichment of emulated threats across the enterprise security ecosystem to reduce risk, improve efficiency and enable an open cybersecurity ecosystem.
1 hour
Validated hundreds of TTPs
It was easy for us to start with the FourCore ATTACK platform and automate adversary simulation in minutes. FourCore ATTACK offered a complete breach assessment, and we uncovered various security misconfigurations on protected endpoints.Nitin SLead - Solution Design, SecureInteli27
Exposures discovered in just 3 hours
We used FourCore ATTACK once and found a serious security issue that had been around in our infrastructure for a long time. This helped us fix it quickly in our endpoints and optimize our email solutions without wasting any resources.Security HeadRenewable Energy Leader in India600+
TTP Simulations With FourCore ATTACK
FourCore ATTACK adversary simulations helps us to effectively showcase our SOC detection capabilities, test incident response procedures and also enhance the rules that we define for our customers. Our turnaround time for testing has greatly improved by using FourCore.Kalpesh SurjianiCo-Founder, Head MSSP & GRC, CyberNX50%
SOC KPI Optimization
FourCore ATTACK has been a valuable tool for our SOC team. We have been training our analysts and trainees with FourCore ATTACK. It has helped us identify areas where our team needed improvement in defending against real-world attacks.Sachin AnandSOC Manager - Plus971 Cybersecurity
Discover Our Latest Resources

Validate Your Security Controls
Build observability of your defense surface. Get started with FourCore ATTACK and emulate threats to assess, validate and improve your security controls.
Stay in Touch
Subscribe to our newsletter for the latest updates.
By signing up to our newsletter you agree to our Term of Service and Privacy Policy




![Threat Hunting: Detecting Browser Credential Stealing [T1555.003] Blog Post Image](/_next/image?url=%2Fimages%2Fbrowsercreds_threathunting%2Fheader.png&w=3840&q=75)